Accessing the Workshop cloud computing environment
Quick start
Changing your password
Change your password through the web by going to https://workshop.colorado.edu, and clicking on the “Password change” card, or by going directly to https://workshop.colorado.edu/lum.
Command line access
- Use your preferred SSH client
- Or use the web based ssh client at https://workshop.colorado.edu/ssh
- Connect to workshop.colorado.edu with your preferred SSH client (the web client automatically connects to the appropriate server)
- Login with your Workshop username and password
RStudio
- Connect to the cloud environment landing page at https://workshop.colorado.edu and click on the “Rstudio” card
- Or connect directly to https://workshop.colorado.edu/rstudio
- Login with your provided username and password, or your new password if you changed it
Jupyterhub
- Connect to the cloud environment landing page at https://workshop.colorado.edu and click on the “Jupyterhub” card
- Or connect directly to https://workshop.colorado.edu/jupyterhub
- Login with your provided username and password, or your new password if you changed it
- It may take 10-30 seconds for your instance to start, so do not reload or navigate away from the "Your server is starting up" page
Detailed Instructions
Here is a brief video walk through for accessing the cloud computing environment.
RStudio Server
RStudio Server is an R development environment that is accessed with a web browser. All of the R based practicals will be done with RStudio Server running in the Workshop cloud environment. RStudio can also be used to edit and view files in the Workshop cloud environment.
- Using a computer with an up to date web browser, go to https://workshop.colorado.edu and click on the “Rstudio” card
- Or go directly to https://workshop.colorado.edu/rstudio
- Login with your provided username and password, or your new password if you changed it
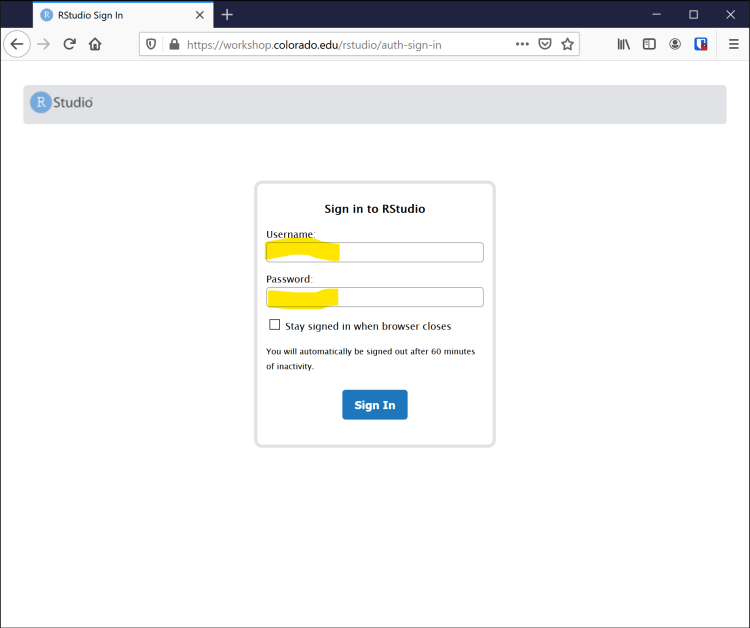
RStudio authentication page
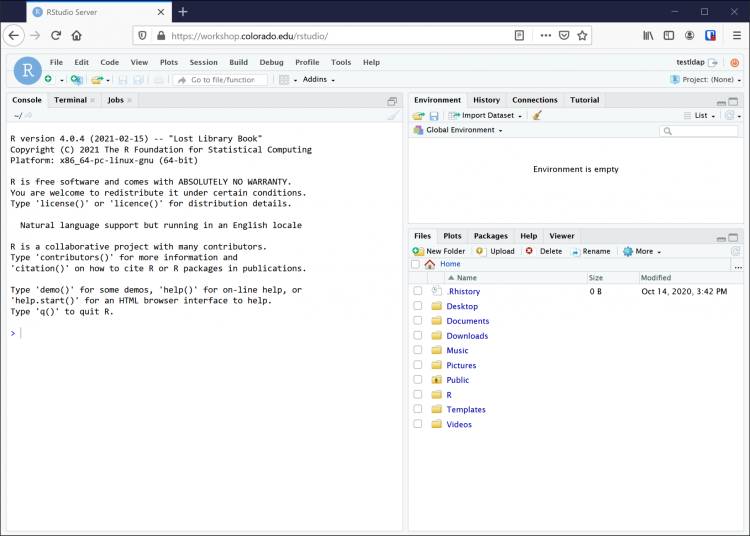
RStudio page
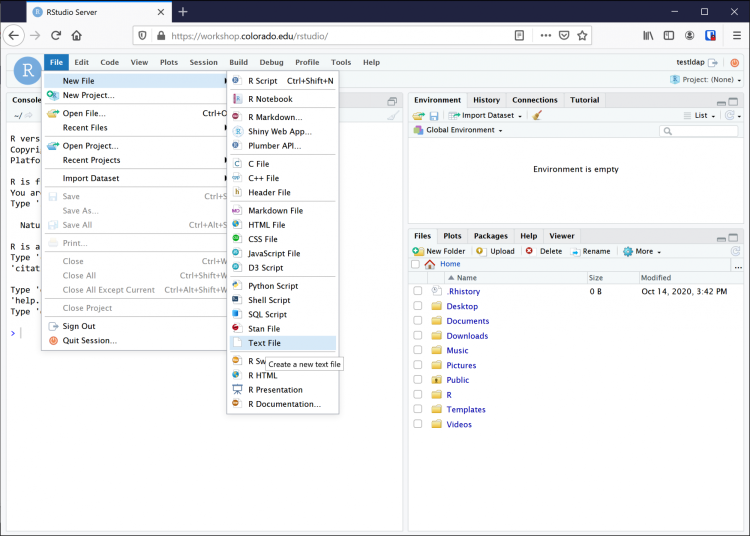
Using RStudio to create an empty text file
Command line access
Some of the practicals require command line access to the Workshop cloud environment. Command line access is obtained using the SSH protocol. There are many “SSH clients”, which are programs used to make SSH connections. If you have preferred one, then use that one.
The Workshop cloud environment is setup so that connections to workshop.colorado.edu are spread out to the different compute nodes in the cloud. When logged in your command prompt will appear similar to
username@ip-10-0-201-180:~$
which means you are logged into a cloud node at the private address 10.0.201.180. Repeated logins may or may not connect to the same node. Which node you connect to is not important, as all files and programs are available from every node.
Web based SSH
A web based SSH client has been provided. It automatically connects to the Workshop cloud computing environment. To access the web based SSH client go to https://workshop.colorado.edu and click on the “SSH” card, or go directly to the SSH page at https://workshop.colorado.edu/ssh.
The web based SSH client requires no additional software (other than a web browser) on your local computer, but you must keep the browser and tab open for the entire time you want to use the command line.
Apple macOS and Linux
These instructions apply to all versions of macOS and distributions of Linux.
Builtin SSH client
Linux and macOS come with a builtin SSH client that is run from the command line.
A brief video demonstrating using SSH from a Mac Terminal window is available.
- Open a terminal window
- On macOS, use Spotlight to search for the program terminal and run it, or find it under Applications -> Utilities -> Terminal
- On Linux, open a terminal such as gnome-terminal, konsole, xfce4-terminal, or any of many others
- At the command prompt type ssh username@workshop.colorado.edu
- Where "username" is the Workshop username that you have been provided
- For example, if your username is “student12” then type ssh student12@workshop.colorado.edu
- The first time you connect you will be asked to verify workshop.colorado.edu. See the SSH fingerprints section for information. It is generally safe to answer yes.
Microsoft Windows 10 and 11
On Windows computers it is recommended that a third party SSH client is used.
PuTTY
A brief video demonstrating installing PuTTY and using it to connect to the Workshup cluster is available.
PuTTY is a popular SSH client for Windows (and other operating systems).
- Installation
- Download from the PuTTY website
- You probably want the “MSI (‘Windows Installer’)” 64-bit version
- It will be a file named putty-64bit-0.76-installer.msi, but possibly with a different version number
- Once the file is downloaded, run it to install PuTTY
- It is safe to accept the default options
- Click “Next” through the install wizard, until it finishes
- Using PuTTY
- By default, PuTTY can be found in the “Start” menu under “PuTTY (64-bit) -> PuTTY”
- Running PuTTY will open the PuTTY Configuration window
- Enter workshop.colorado.edu into the “Host Name” field
- Click “OK”, or press enter
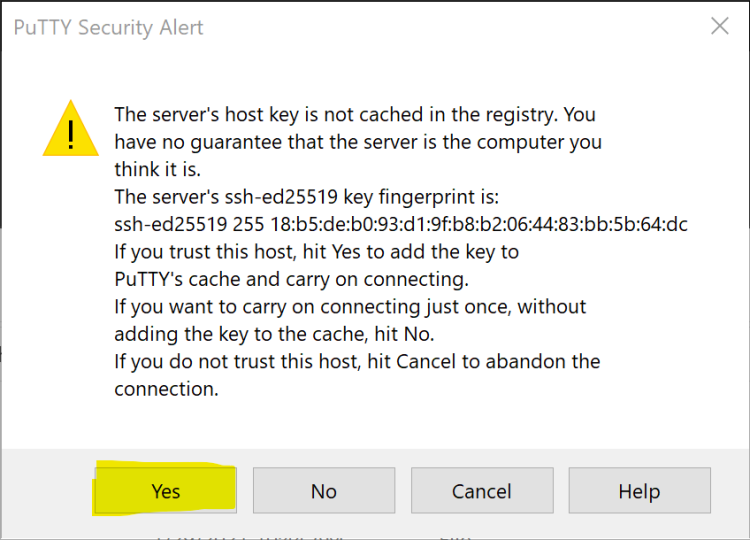
- The PuTTY Security Alert window will be shown on the first connection. It is usually safe to click “Yes”, but see the SSH fingerprints section for a full explanation.
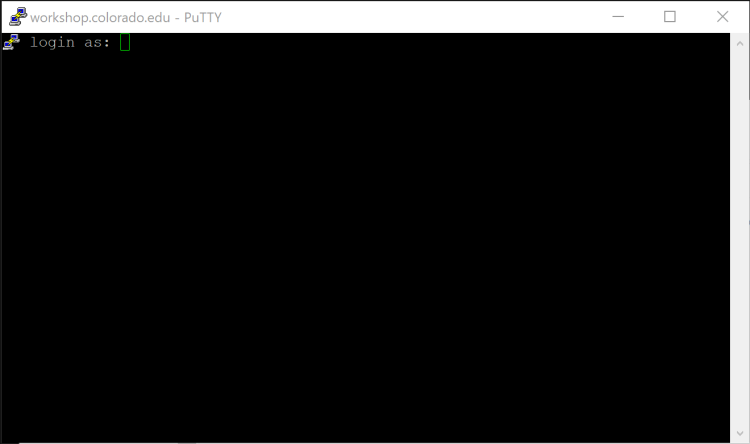
- The PuTTY terminal window will open with the prompt login as:
- Enter your Workshop username and password
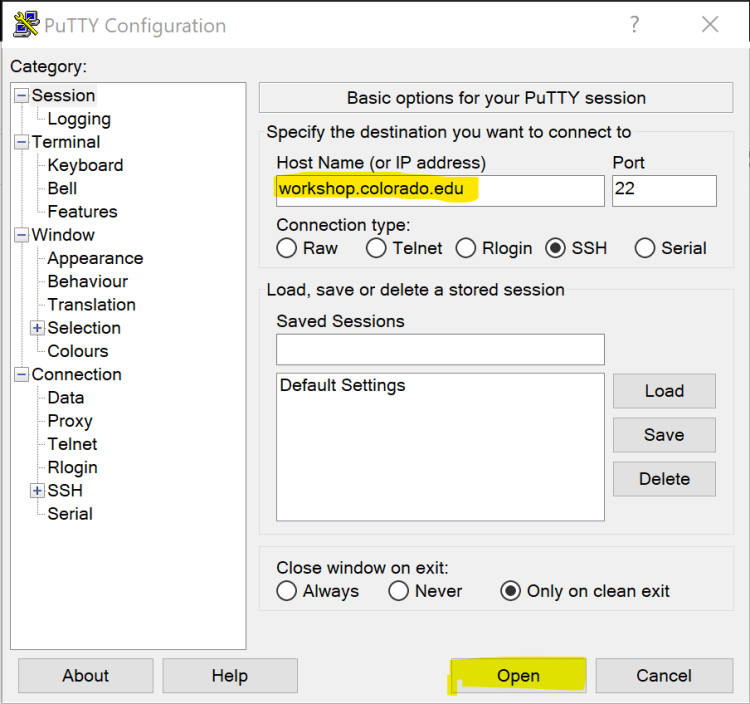
The PuTTY Configuration window
The PuTTY Security Alert window
The PuTTY terminal window
Bitvise SSH client
A brief video demonstrating installing Bitvise and using it to SSH to the Workshop cluster is available.
Bitvise is another popular SSH client for Windows. It is somewhat more complicated to setup than PuTTY, but has more features.
- Installation
- Download from the Bitvise website
- Click the “Download Bitvise SSH Client installer” button
- Once the program has downloaded, run it to install the Bitvise SSH client
- If you agree to the terms of the license then check the box, and click “Install”
- When the installation completes, click “Ok” to dismiss the installer window
- Using Bitvise SSH Client
- By default, Bitvise SSH Client can be found in the “Start” menu under “Bitvise SSH Client -> Bitvise SSH Client”
- Running it will open the Bitvise SSH Client window
- Create a profile for workshop.colorado.edu
- Click the “New profile” icon
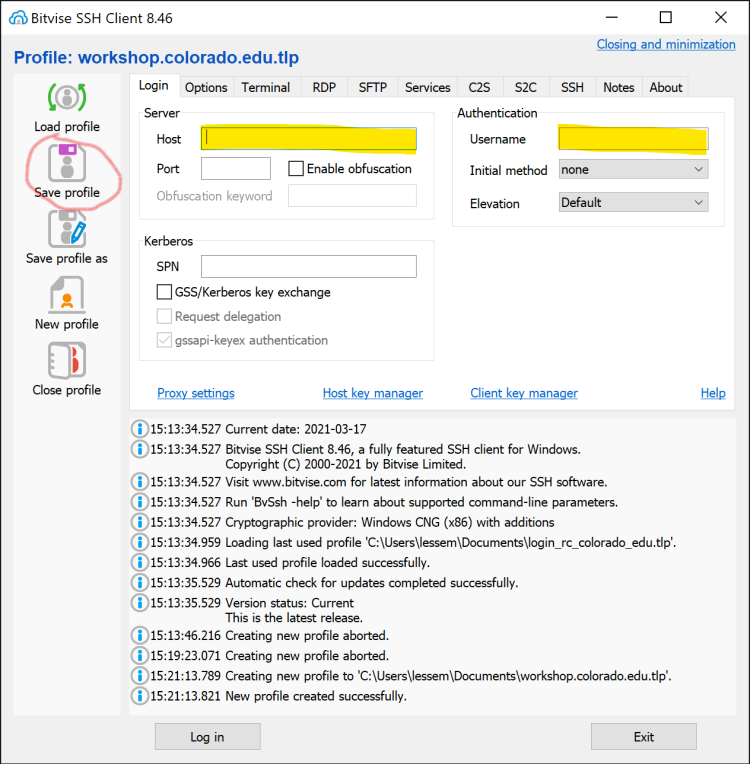
- Enter a name for the profile, such as “workshop.colorado.edu”
- Enter workshop.colorado.edu into the “Host” field
- Enter your Workshop username into the “Username” field
- Click the “Save profile” icon
- When opening a new Bitvise SSH Client session
- Click the “Load profile” icon
- Select the profile you created for the Workshop
- Once the profile is loaded, click the “Log in” button at the bottom of the window
- The first time you connect the “Host Key Verification” window will appear
- It is usually safe to click “Accept and Save”
- See the SSH fingerprints section for a full explanation
- The “User Authentication” window will appear, enter your Workshop password into the “Password” field
- This will create Bitvise terminal and file transfer windows
The Bitvise SSH Client window
Creating the Workshop profile
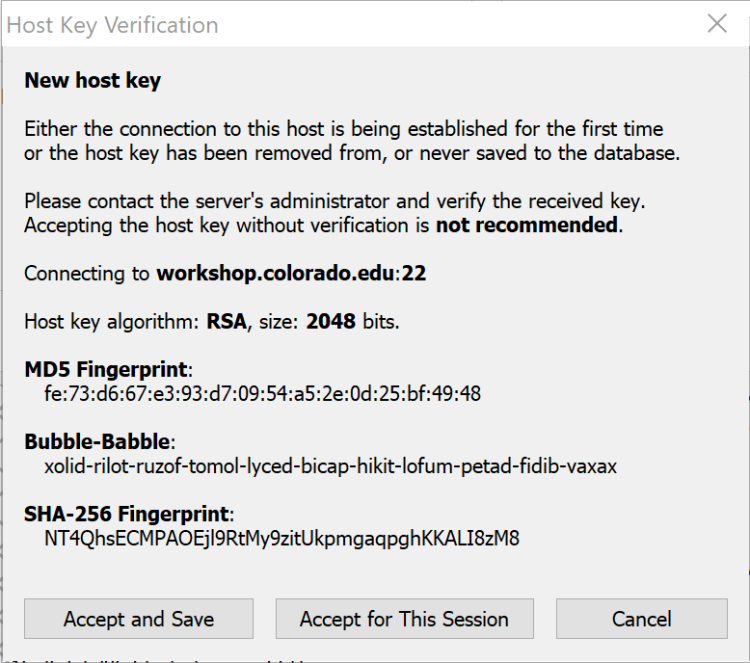
The Host Key Verification window
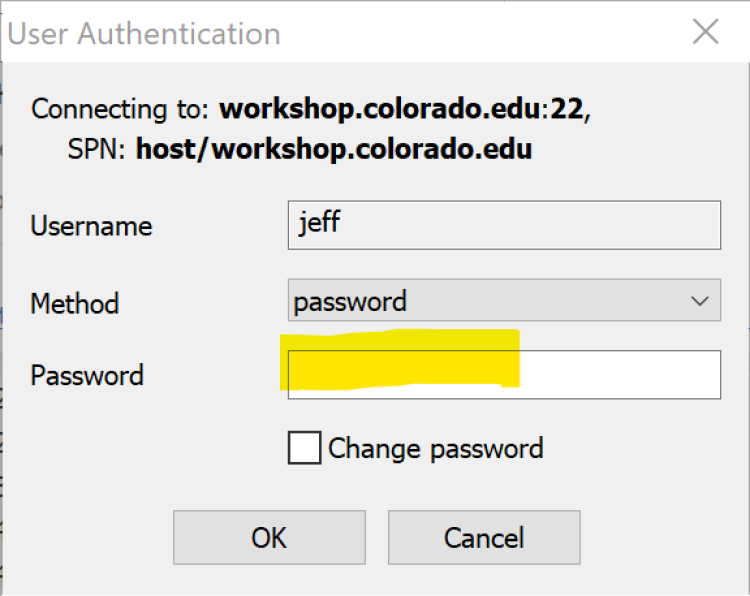
The User Authentication window
The Bitvise terminal window
SSH fingerprints
Mostly, you do not need to worry about this, and can take whatever action is necessary to accept the key, such as typing yes, or clicking OK.
The first time you connect to workshop.colorado.edu you will be asked a question similar to:
The authenticity of host 'workshop.colorado.edu (128.138.139.65)' can't be established. ECDSA key fingerprint is SHA256:7aZtwMf1EfXZEnGYY3bpUErTdLh1LJ3Yq8ka6Zkc53Q. Are you sure you want to continue connecting (yes/no/[fingerprint])?
The SSH client is asking you to verify the key fingeprint is the unique fingerprint of workshop.colorado.edu. There are several different types of keys, and depending on the SSH client used, a different key might be presented. The key fingerprint table lists all of them.
SSH key fingerprints for workshop.colorado.edu
| Key | SHA256 Fingerprint |
|---|---|
| ECDSA | 7aZtwMf1EfXZEnGYY3bpUErTdLh1LJ3Yq8ka6Zkc53Q |
| ED25519 | UM89YHOoZlP6vM4Yj0qNg+zx9+POszYjHkMxGjoOO6k |
| RSA | NT4QhsECMPAOEjl9RtMy9zitUkpmgaqpghKKALI8zM8 |
| Key | MD5 Fingerprint |
|---|---|
| ECDSA | 11:9f:ff:24:a5:e1:fc:7a:a6:ee:46:ec:d6:bd:7a:e3 |
| ED25519 | 18:b5:de:b0:93:d1:9f:b8:b2:06:44:83:bb:5b:64:dc |
| RSA | fe:73:d6:67:e3:93:d7:09:54:a5:2e:0d:25:bf:49:48 |

